Modern AI systems — especially self-learning AI — don’t just train once and run. They continuously learn from real-world data to adapt, improve, and make smarter decisions in real time.
But with continuous learning comes serious challenges:
 Data is pulled from dozens of sources: APIs, web, IoT devices, system logs…
Data is pulled from dozens of sources: APIs, web, IoT devices, system logs… Security risks increase: training data can be blocked, throttled, corrupted, or stolen.
Security risks increase: training data can be blocked, throttled, corrupted, or stolen. Performance suffers without proper traffic control and routing layers.
Performance suffers without proper traffic control and routing layers.

- Recommendation Engines adapt to real-time user behavior.
- Medical AI learns from ongoing clinical data across hospitals.
- Federated/Edge Learning requires constant input from thousands of decentralized edge devices.
 IP bans while scraping open data or public APIs (common in NLP, LLM model training).
IP bans while scraping open data or public APIs (common in NLP, LLM model training). Training data leaks from unverified sources.
Training data leaks from unverified sources. Bandwidth congestion when too many data requests hit centralized pipelines.
Bandwidth congestion when too many data requests hit centralized pipelines.

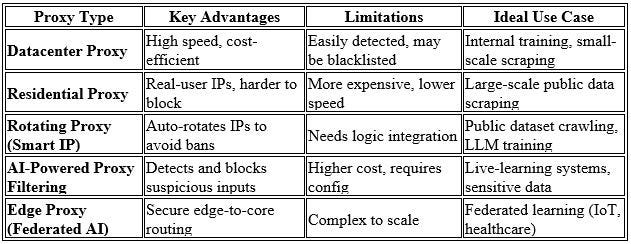
Proxy in AI infrastructure acts as a “smart traffic orchestrator” — filtering, directing, and protecting your AI’s learning flow.
 Blocks unreliable or malicious data sources before they enter training pipelines.
Blocks unreliable or malicious data sources before they enter training pipelines. Rotates IPs during data collection from open web/API to avoid blocks or throttling.
Rotates IPs during data collection from open web/API to avoid blocks or throttling. Prioritizes critical traffic and bandwidth for real-time model updates.
Prioritizes critical traffic and bandwidth for real-time model updates. Combines AI into proxy to detect abnormal traffic patterns and auto-adjust filters.
Combines AI into proxy to detect abnormal traffic patterns and auto-adjust filters.
- Meta (2023) used rotating proxy pools to scrape multilingual datasets from over 2 million websites while building foundational LLMs.
- Tesla integrates edge proxies in its autonomous vehicles to secure data transfer between sensors and cloud-based AI models.
- Google DeepMind deployed intelligent proxy filters to optimize cloud-to-cluster bandwidth and reduce training noise.
ProxyAZ delivers enterprise-grade proxy services optimized for AI applications:
 Over 9 million IPs (residential, datacenter, ISP) across 60+ countries
Over 9 million IPs (residential, datacenter, ISP) across 60+ countries Smart IP rotation and geo-targeted routing, ideal for training data collection
Smart IP rotation and geo-targeted routing, ideal for training data collection AI-enhanced traffic analysis to detect malicious input or API abuse
AI-enhanced traffic analysis to detect malicious input or API abuse Elastic scaling to handle data spikes during model updates or retraining
Elastic scaling to handle data spikes during model updates or retraining Full compatibility with cloud-native, containerized, and edge architectures
Full compatibility with cloud-native, containerized, and edge architectures
In self-learning AI environments:
- Data flow is the nervous system
- Proxy is the immune system
- The combination enables secure, scalable, and real-time model improvement.
“Real-Time Threat Detection with Proxy + AI — How to Secure Learning Pipelines from Sophisticated Attacks”

